- The catch with InfiniteWP is the expensive premium add-ons, which can end up costing you an arm and a leg per add-on. They do offer bundles based on the number of sites, with the most expensive being $447 per year for all add-ons on unlimited sites.
- Description InfiniteWP allows users to manage unlimited number of WordPress sites from their own server.
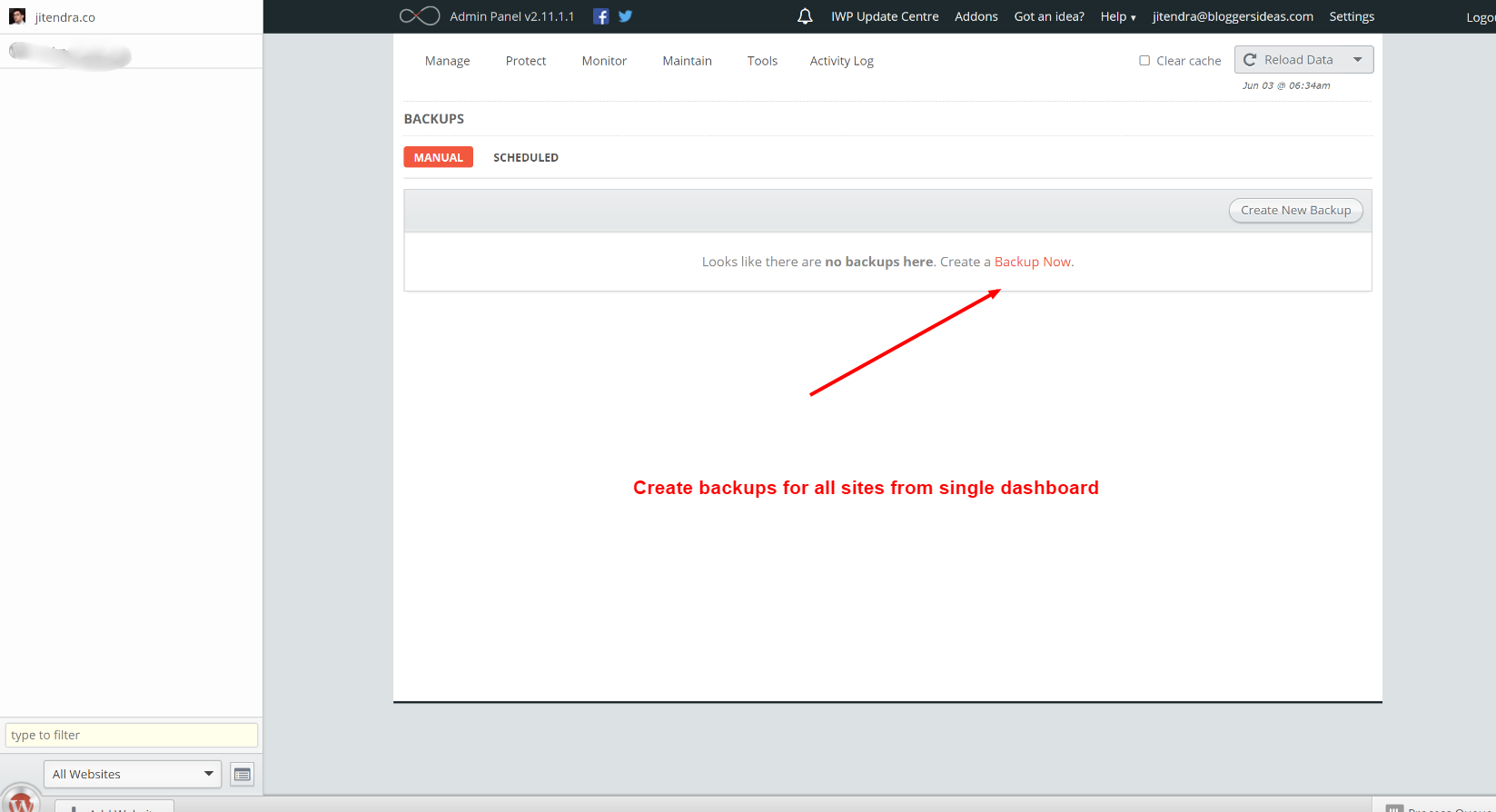
IWP Client Plugin download link - quick how-to on adding your first Wordpress site to InfiniteWP Admin. The latest tweets from @infinitewp.
MS-ISAC ADVISORY NUMBER:
2020-008DATE(S) ISSUED:
01/16/2020OVERVIEW:
A vulnerability has been discovered in the Revmakx InfiniteWP Client Plugin that could allow for authentication bypass. WordPress is a web-based publishing application implemented in PHP, and the Revmakx InfiniteWP Client Plugin allows website administrators to manage an unlimited number of WordPress sites from a centralized management server. Successful exploitation of this vulnerability could allow for authentication bypass with admin privileges.
THREAT INTELLIGENCE:
On January 14th, WebARX published a proof-of-concept for this flaw in WordPress InfiniteWP Client Plugin. The PoC is available at https://www.webarxsecurity.com/vulnerability-infinitewp-client-wp-time-capsule/
SYSTEMS AFFECTED:
- Revmakx InfiniteWP Client Plugin prior to 1.9.4.5
RISK:
Government:
- Large and medium government entities: HIGH
- Small government entities: MEDIUM
Infinitewp Plugin
Businesses:
- Large and medium business entities: HIGH
- Small business entities: MEDIUM
Home Users:
LOWTECHNICAL SUMMARY:
A vulnerability has been discovered in the Revmakx InfiniteWP Client Plugin that could allow for authentication bypass. This vulnerability exists because the plugin fails to properly authenticate users accessing the iwp_mmb_set_request function in the init.php file. An unauthenticated attacker can exploit this issue by encoding the payload containing the admin username with JSON, then Base64 and sending it via POST request to the affected site. Successful exploitation of this vulnerability could allow for authentication bypass with admin privileges.
RECOMMENDATIONS:
We recommend the following actions be taken:
- Apply appropriate updates provided by Revmakx manually to affected systems, immediately after appropriate testing.
- Apply the Principle of Least Privilege to all systems and services.
- Verify no unauthorized system modifications have occurred on system before applying patch.
- Monitor intrusion detection systems for any signs of anomalous activity.
- Unless required, limit external network access to affected products.
REFERENCES:
WordPress:
https://wordpress.org/plugins/iwp-client/Bleeping Computer:
https://www.bleepingcomputer.com/news/security/critical-wordpress-plugin-bug-allows-admin-logins-without-password/Information Hub : Advisories
Wordpress Site Management

Infinitewp Multisite
Infinitewp Review
